- Mesaj
- 19
- Beğeni
- 2
- Puan
- 40
- Ticaret Puanı
- 0
Merhaba öncelikle , Sıfırdan metin2 server files hazırlama rehberinde bir yerde takılı kalmış durumdayım. Kodlamadan anlamam öncelikle bunu belirteyim.Videoda ki gibi ilerleme yapıyordum lakin bende bir sürü hata çıktı. Bunları sebini anlamış değilim. Cryptopp sürümünü yükselttik. Resimde gözüktüğü gibi yaptım bende ama çare bulamadım. Yardımcı olacak arkadaşlara şimdiden teşekkür ederim.
Çıktı :
Yeniden derleme işlemi başladı...
1>------ Tümü Yeniden Derle başladı: Proje: eterBase, Yapılandırma: Release Win32 ------
1>Base.cpp
1>Poly.cpp
1>Symbol.cpp
1>SymTable.cpp
1>cipher.cpp
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(35,88): error C2059: sözdizimi hatası: ')'
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(38,3): error C2628: 'Cipher' arkasından 'void' gelmesi geçersizdir (bir ';' mü unuttunuz?)
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(40,10): error C2065: 'activated_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(41,7): error C2561: 'Decrypt': işlev bir değer döndürmelidir
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(38): message : 'Decrypt' bildirimine bakın
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(43,5): error C2065: 'decoder_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(32,10): error C2065: 'activated_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(35,5): error C2065: 'encoder_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(35,42): error C2059: sözdizimi hatası: ')'
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(46,26): error C2270: 'activated': üye olmayan işlevlerde değiştiricilere izin verilmez
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(46,35): error C2065: 'activated_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(48,36): error C2065: 'activated_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(50,2): error C2059: sözdizimi hatası: 'private'
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(59,1): error C2059: sözdizimi hatası: '}'
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(59,1): error C2143: sözdizimi hatası: ';' eksik ('}' öncesinde)
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(137,3): error C2614: 'Cipher': geçersiz üye başlatma: 'activated_' bir taban veya üye değil
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(137,22): error C2614: 'Cipher': geçersiz üye başlatma: 'encoder_' bir taban veya üye değil
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(137,38): error C2614: 'Cipher': geçersiz üye başlatma: 'decoder_' bir taban veya üye değil
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(137,54): error C2614: 'Cipher': geçersiz üye başlatma: 'key_agreement_' bir taban veya üye değil
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(203,14): error C2039: 'SetUp': bir 'Cipher' üyesi değil
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(16): message : 'Cipher' bildirimine bakın
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(446,17): warning C4193: #pragma warning(pop): eşleşen '#pragma warning(push)' yok
1>CPostIt.cpp
1>CRC32.cpp
1>Debug.cpp
1>error.cpp
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\error.cpp(59,23): warning C4477: 'fprintf' : '%08x' biçim dizesi 'unsigned int' türü bir bağımsız değişken gerektirir, ancak 1 değişen sayıda bağımsız değişkenin türü 'time_t'
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\error.cpp(59,23): message : biçim dizesinde '%llx' kullanmayı düşünün
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\error.cpp(59,23): message : biçim dizesinde '%I64x' kullanmayı düşünün
1>FileBase.cpp
1>FileDir.cpp
1>FileLoader.cpp
1>lzo.cpp
1>MappedFile.cpp
1>Random.cpp
1>StdAfx.cpp
1>Stl.cpp
1>tea.cpp
1>TempFile.cpp
1>Timer.cpp
1>Kod Üretiliyor...
1>Derleniyor...
1>Utils.cpp
1>Kod Üretiliyor...
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\Utils.cpp(627): warning C4706: koşullu ifadeyle atama
1>"eterBase_VC90.vcxproj" projesini oluşturma tamamlandı -- BAŞARISIZ OLDU.
========== Tümünü Yeniden Oluşturma: 0 başarılı, 1 başarısız, 0 atlandı ==========
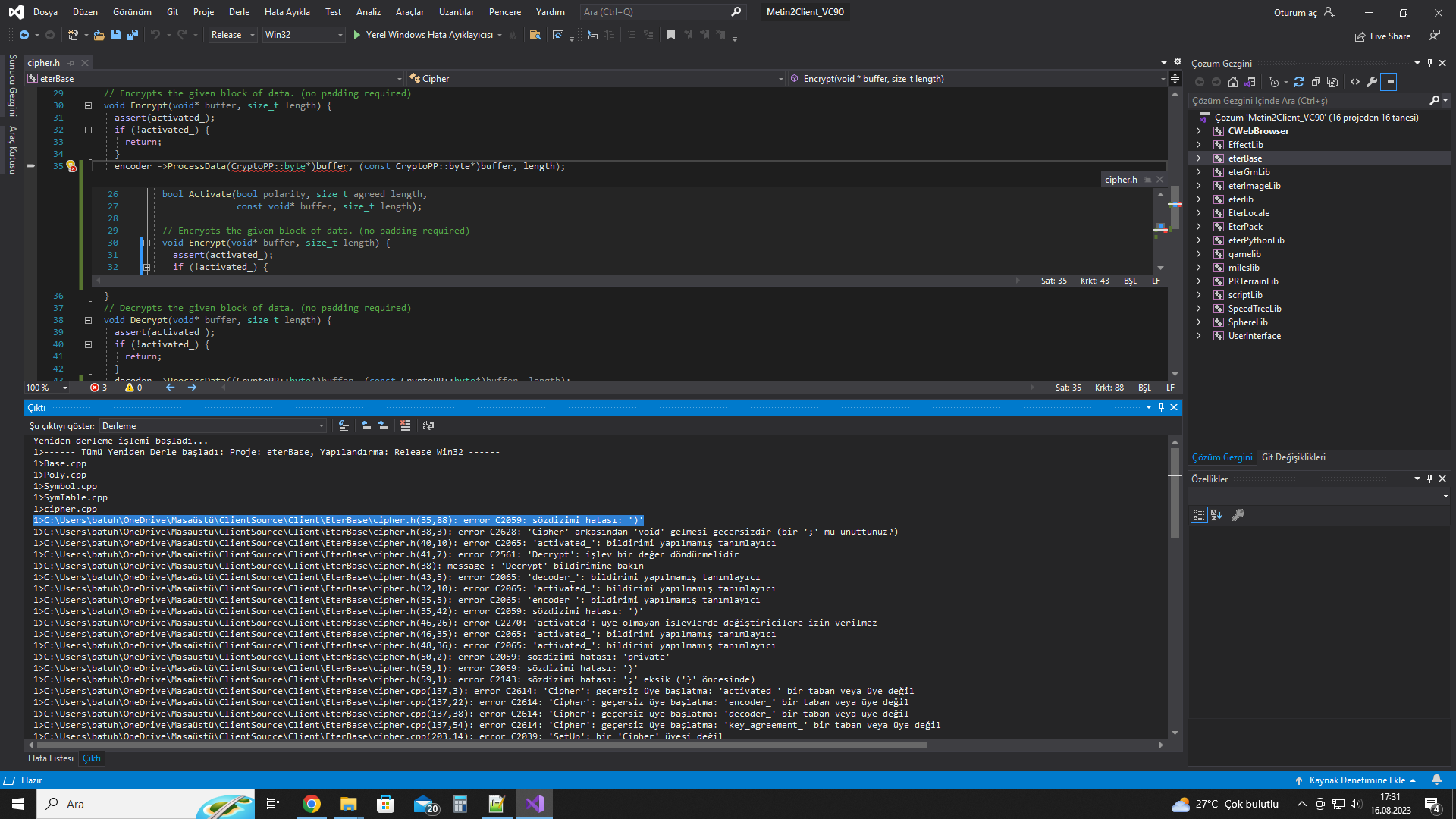
Çıktı :
Yeniden derleme işlemi başladı...
1>------ Tümü Yeniden Derle başladı: Proje: eterBase, Yapılandırma: Release Win32 ------
1>Base.cpp
1>Poly.cpp
1>Symbol.cpp
1>SymTable.cpp
1>cipher.cpp
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(35,88): error C2059: sözdizimi hatası: ')'
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(38,3): error C2628: 'Cipher' arkasından 'void' gelmesi geçersizdir (bir ';' mü unuttunuz?)
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(40,10): error C2065: 'activated_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(41,7): error C2561: 'Decrypt': işlev bir değer döndürmelidir
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(38): message : 'Decrypt' bildirimine bakın
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(43,5): error C2065: 'decoder_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(32,10): error C2065: 'activated_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(35,5): error C2065: 'encoder_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(35,42): error C2059: sözdizimi hatası: ')'
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(46,26): error C2270: 'activated': üye olmayan işlevlerde değiştiricilere izin verilmez
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(46,35): error C2065: 'activated_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(48,36): error C2065: 'activated_': bildirimi yapılmamış tanımlayıcı
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(50,2): error C2059: sözdizimi hatası: 'private'
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(59,1): error C2059: sözdizimi hatası: '}'
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(59,1): error C2143: sözdizimi hatası: ';' eksik ('}' öncesinde)
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(137,3): error C2614: 'Cipher': geçersiz üye başlatma: 'activated_' bir taban veya üye değil
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(137,22): error C2614: 'Cipher': geçersiz üye başlatma: 'encoder_' bir taban veya üye değil
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(137,38): error C2614: 'Cipher': geçersiz üye başlatma: 'decoder_' bir taban veya üye değil
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(137,54): error C2614: 'Cipher': geçersiz üye başlatma: 'key_agreement_' bir taban veya üye değil
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(203,14): error C2039: 'SetUp': bir 'Cipher' üyesi değil
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.h(16): message : 'Cipher' bildirimine bakın
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\cipher.cpp(446,17): warning C4193: #pragma warning(pop): eşleşen '#pragma warning(push)' yok
1>CPostIt.cpp
1>CRC32.cpp
1>Debug.cpp
1>error.cpp
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\error.cpp(59,23): warning C4477: 'fprintf' : '%08x' biçim dizesi 'unsigned int' türü bir bağımsız değişken gerektirir, ancak 1 değişen sayıda bağımsız değişkenin türü 'time_t'
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\error.cpp(59,23): message : biçim dizesinde '%llx' kullanmayı düşünün
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\error.cpp(59,23): message : biçim dizesinde '%I64x' kullanmayı düşünün
1>FileBase.cpp
1>FileDir.cpp
1>FileLoader.cpp
1>lzo.cpp
1>MappedFile.cpp
1>Random.cpp
1>StdAfx.cpp
1>Stl.cpp
1>tea.cpp
1>TempFile.cpp
1>Timer.cpp
1>Kod Üretiliyor...
1>Derleniyor...
1>Utils.cpp
1>Kod Üretiliyor...
1>C:\Users\batuh\OneDrive\Masaüstü\ClientSource\Client\EterBase\Utils.cpp(627): warning C4706: koşullu ifadeyle atama
1>"eterBase_VC90.vcxproj" projesini oluşturma tamamlandı -- BAŞARISIZ OLDU.
========== Tümünü Yeniden Oluşturma: 0 başarılı, 1 başarısız, 0 atlandı ==========
